First and foremost, we urge you to get in touch with us if you are experiencing any unusual or suspicious activity on your CM.com account. We will take every measure necessary to protect your data and accounts, but you can help us as well with preventative measures. In this blog, we signpost some of the most prevalent types of fraud you might encounter, and what you can put in place to minimize the risks.
Fraudsters need to communicate at scale with their potential victims and if they can do this for free by piggybacking off your CM.com account so much the better – for them. The risk of account compromise can be tackled in different ways which we shall look at next.
Why Do Criminals Want to Compromise My CM.com Account?
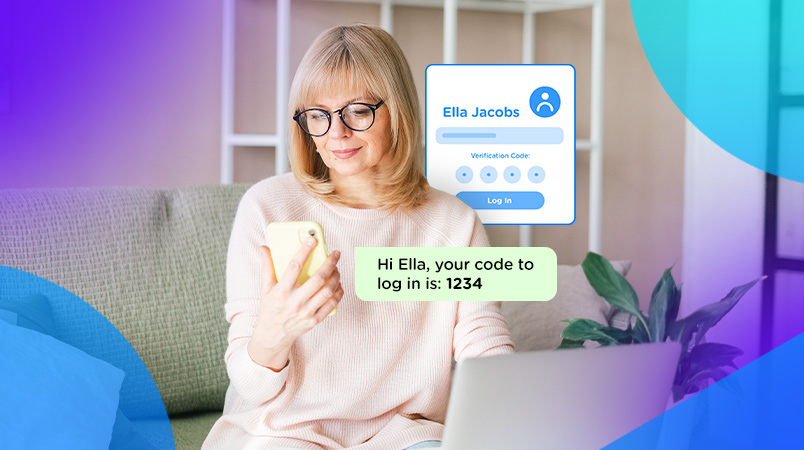
We are all familiar with the threat of phishing: fraudulent emails and websites designed to trick recipients into revealing sensitive information, especially banking details. Text messages and voice calls are also exploited to “fish” for data, and these techniques are called “smishing” (with the “s” of SMS) and “vishing” for fraudulent voice messages.
 Targeting a CM.com customer account is attractive to the fraudsters for two reasons: they can send out messages for free, and they can hide their identity. If your account is compromised, the fraudulent messages are coming from you.
Targeting a CM.com customer account is attractive to the fraudsters for two reasons: they can send out messages for free, and they can hide their identity. If your account is compromised, the fraudulent messages are coming from you.
Next to phishing, smishing and vishing, fraudsters may also try to leverage your account to initiate voice calls to premium rate numbers – for which the CM.com account holder will then be charged.
Of course, there are things you can – and must – do to prevent criminals from cracking your account credentials or stealing your API token. We list these below.
What Can You Do to Prevent Account Compromise?
Ensure that two-factor authentication (2FA) is enabled on your CM.com account. This feature substantially decreases the likelihood of unauthorized access compared with an account that is protected solely with a username and password.
Create a complex password or even a passphrase using a combination of words, numbers, symbols, and upper and lower letters. Avoid using personal information or words that can be found in the dictionary.
Never share your token online or with someone who doesn’t need it. Your token must stay secured on your own servers; under no condition should it be shown to the end users of your website, not even in encrypted form. Your token should not be included in the source code of your website or mobile app.
Set a limit to your monthly credit amount and increase it when needed for a campaign by contacting your CM.com account manager. When you reach 75% of your credit you will automatically be notified by email. When 100% is reached, your account will be temporarily suspended and reactivated once the outstanding invoices are settled.
SMS Pumping and Toll Fraud
Account compromise is not the only fraud risk in conversational commerce; you also need to protect against so-called SMS pumping and toll fraud where the fraudster abuses your website and the verification possibilities.
What is SMS Pumping?
In SMS pumping, traffic pumping, or Artificially Inflated Traffic (AIT), fraudsters exploit automated log-in systems to trigger sharp spikes in traffic toward numbers they own or to a range of numbers controlled by a specific mobile network operator (MNO) with whom they conspire. The fraudsters reap a share of the revenue generated in this way, but the CM.com account holder gets to foot the bill.
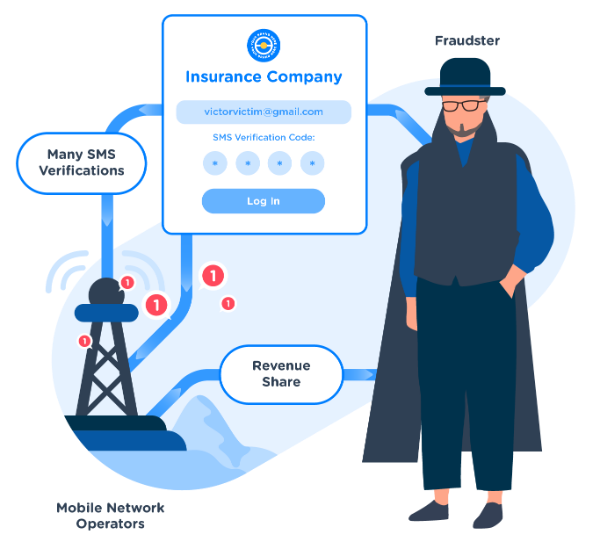 Look out for a spike of messages sent to a block of consecutive numbers (i.e. +1234567890, +1234567891, +1234567892, +1234567893 and so on). These numbers are most probably controlled by the same MNO. A telltale sign for fraudulent use of a one-time SMS passcode is an incomplete verification cycle. Unfortunately, advanced fraudsters even have the tools to fake a completed verification cycle.
Look out for a spike of messages sent to a block of consecutive numbers (i.e. +1234567890, +1234567891, +1234567892, +1234567893 and so on). These numbers are most probably controlled by the same MNO. A telltale sign for fraudulent use of a one-time SMS passcode is an incomplete verification cycle. Unfortunately, advanced fraudsters even have the tools to fake a completed verification cycle.
What is Toll Fraud?
In the scenario of toll fraud, criminals target phone verification to generate a high volume of voice calls to premium rate numbers, which charge callers a price per call or per minute. If such calls are fraudulently generated from your website(s) the charges fall on you.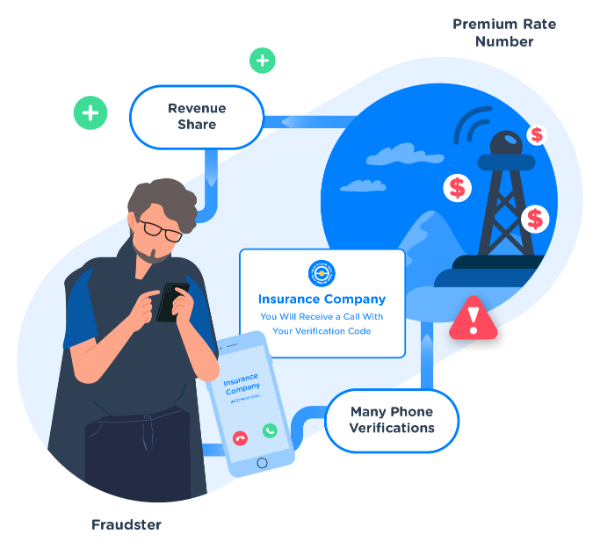
What Can You Do to Prevent or Detect SMS Pumping and Toll Fraud?
Detect and deter bot attacks by implementing libraries such as BOTD or CAPTCHAs on your website.
Monitor one-time passcode (OTP) conversion rates and create alerts as rates are dropping.
Implement (exponential) delays between verification retry requests with the same phone number.
Offer alternative channels such as voice verification, not in the first instance but for example on the third verification attempt.
Build a destination “allow” or “block” list on your website.
Analyze IP and detect VPNs on your website.
Implement rate limits on the number of requests. For example, limit the number of requests per phone number/IP address over a set time period on your website.
Set a limit to your monthly credit amount as outlined above.
Fraud is a sad fact of life, and criminals are always looking for new ways to exploit innovative technologies. If you want to know what CM.com does to protect against security breaches, visit our Trust Center.
We hope this short blog will have given you a better idea about the fraud risks in conversational commerce, and what you can do to mitigate them. If you believe your account could have been compromised or suspect any other type of malfeasance, please get in touch.